
Pritunl is an open source management interface for OpenVPN. It allows for private networks, has native IPv6 support, and is relatively simple to use.
That said, it also receives regular updates, and allows for full customization. In addition to the features above, custom routes are supported, and key size can be selected for increased performance.
In order to install Pritunl, you'll need:
whoami).nano or vim (text editor).In order to install Pritunl, we'll need to add the necessary repositories to yum. Yum is essentially the package manager for CentOS and RHEL systems. It is similar to apt-get, so don't worry if this is your first time.
We'll be using nano for this tutorial, but you may use vim, if you prefer.
The first thing we'll be doing is adding the MongoDB repository:
nano /etc/yum.repos.d/mongodb-org-3.4.repoOnce you've entered the file, it should be blank. Paste the following in:
[mongodb-org-3.4]
name=MongoDB Repository
baseurl=https://repo.mongodb.org/yum/redhat/7/mongodb-org/3.4/x86_64/
gpgcheck=1
enabled=1
gpgkey=https://www.mongodb.org/static/pgp/server-3.4.ascExit and save by pressing CTRL and O simultaneously. Once you do, simply press the "enter" key.
Now that we've added the repository for MongoDB (database software for Pritunl), we need to add the Pritunl repository.
nano /etc/yum.repos.d/pritunl.repoWhen the file loads in your text editor, paste the following:
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/stable/yum/centos/7/
gpgcheck=1
enabled=1Exit and save.
Continuing on, we need to install epel-release:
yum -y install epel-releaseWe now have all of the dependencies required. We'll need to disable SELinux before continuing:
nano /etc/selinux/configIt should say the following once opened:
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=enforcing .
# SELINUXTYPE= can take one of three two values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targetedChange the SELINUX=enforcing line to SELINUX=disabled.
Reboot your server, and log back in.
We've added all of the necessary packages and changed the necessary settings to install Pritunl.
Before we install, we need to add some keys (necessary for the repositories to function):
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > temp.tmp; sudo rpm --import temp.tmpWe can now delete the temporary key:
rm -f temp.tmpNow, we'll run yum to install Pritunl:
yum -y install pritunl mongodb-orgOnce yum finishes, we'll make it so Pritunl and MongoDB run on startup:
systemctl start mongod pritunl
systemctl enable mongod pritunlPritunl is now installed.
After installing Pritunl, run the following:
pritunl setup-keyMake note of the key that comes from running the command above.
Now, visit your server:
https://YOUR_IP_ADDRESSYou should see the following:
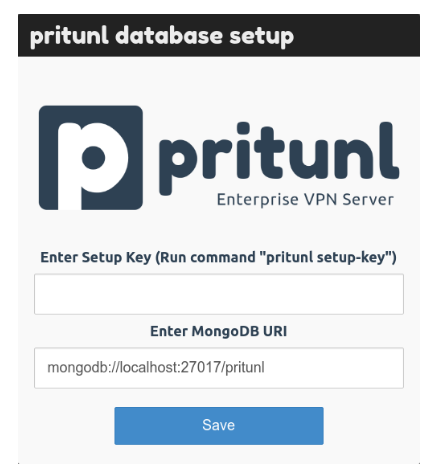
Paste the key that you were given from pritunl setup-key.
Once you hit the "Save" button, you will be prompted to set credentials. You will then be redirected to the login page:
Sign in with your credentials. Proceed to the next section on adding users, and creating your first VPN server.
If you wish to allow other users (whether it be a friend, or colleague), click the "Users" link on the navigation bar:

You should have created an organization already, and creating a user is simple. Click "Add User", and you will be prompted with the following:
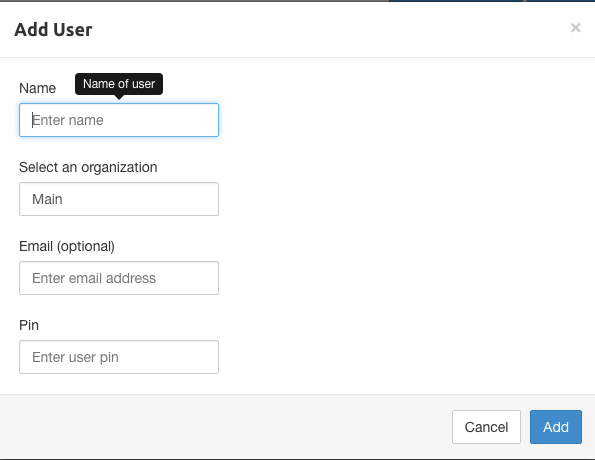
As mentioned previously, Pritunl simply manages OpenVPN.
Head to the "Servers" tab in the navigation bar and click "Add Server." You will be prompted with the following:
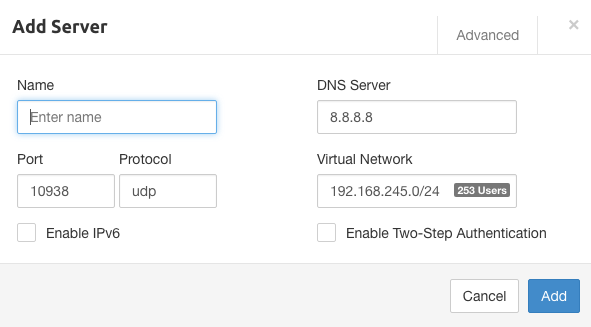
Fill in the fields with the appropriate information. You may choose the protocol (UDP is better for speed, and shorter distances), local IP range, and other options available through the "Advanced" tab.
Once you hit "Add," the dialog will close. After it does, click "Attach Organization".
Select the organization we created in the previous section, and the VPN server created in this section.
Hit "Attach."
As Pritunl uses OpenVPN, connecting should be a breeze. You can choose to install the Pritunl client, or the standalone OpenVPN client.
Note: Installing a client is necessary in order to connect.
Before installing the client, proceed back to the "Users" tab in the management interface. You should see icons next to the user you created:

A tar.gz file will begin to download. Upon extraction, you'll receive the profile required to connect. Save the file in a safe place.
You can download the Pritunl client from the official site. The client supports all OpenVPN servers.
For enhanced security, enable two-factor authentication with Pritunl! Two factor authentication is available with Pritunl. It adds the functionality to OpenVPN. You can use Authy, or any supported app to generate the code that you can use to connect.
Congratulations! You've installed and configured your own VPN server.
If you need to uninstall, the process is simple. Run: yum remove -y pritunl mongodb-org
Enjoy!